Least Significant Bit steganography
The first online calculator on this page uses a Least Significant Bit steganographic method to hide a message in a digital image. The second online calculator reveals the message hidden by the first calculator.
You can upload a picture and enter a message - the first calculator below will generate a picture with a message hidden in it. To extract the message from the picture, you need to use the second calculator below - if you load the image generated by the first calculator into it, it will show the message hidden in it. You can read more about steganographic methods of hiding information in digital images below the calculators.
Calculator for adding a message to an image:
Calculator for extracting the message from the image generated by the calculator above:
Steganography in digital images
Steganography is a method of transferring or storing information, taking into account the fact of such transfer (storage) being kept secret. Thus, unlike cryptography, steganography hides the very existence of a secret message. The information is hidden in the carrier object or container, and after adding the message, the carrier object should look "normal", so that the presence of the hidden message in it is invisible to an outside observer. Since steganography does not encrypt hidden information in any way, steganographic methods are used in addition to cryptographic ones.
Steganography can be used to hide information in various types of digital data: text, images, audio and video files. In this sense, digital images represent almost the most popular media object format, since they are large and do not arouse suspicion when published on social networks and sent by e-mail.
Steganographic methods, that is, methods of embedding a secret message in a carrier object, are usually evaluated according to several criteria:
- Imperceptibility - in the case of a digital image, a person should not see the difference between the original image and the image with a secret message embedded in it.
- Embedding capacity - the maximum amount of data that can be inserted into the carrier object.
- Robustness - the ability of a message to resist distortions introduced during processing or transmission of the container object, for example, when compressing or editing (rotating or flipping) an image. Such distortions are sometimes used to purposefully damage the steganogram.
Other characteristics can also be taken into account, for example, resistance to statistical attack (a steganogram should not create a characteristic signature in the host object that can be detected by statistical analysis methods), format independence (the method can be applied to files of different formats), secrecy (difficulty in detecting a steganogram in carrier, if it is known to be there).
Steganographic methods for digital images are divided into two classes: spatial methods (or methods for the time domain) and frequency methods (or methods for the frequency domain). Spatial methods manipulate values in a spatial domain - pixels. Frequency methods - frequency characteristics of the image.
Basic spatial methods:
- LSB, Least Significant Bit
- PVD, Pixel Value Difference
- GLM, Gray Level Modification
- MPV, Mid Position Value
Basic frequency methods:
- DCT, Discrete Cosine Transform
- DWT, Discrete Wavelet Transform
LSB - Least Significant Bit
This method is the simplest method of digital image steganography. The method consists in replacing the least significant bits of the container image with the bits of the message. The logic of the method can be illustrated by the following picture
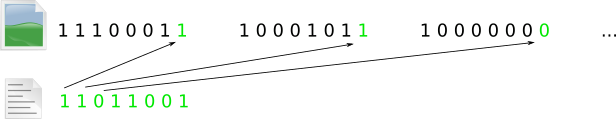
The method has good stealth. A change in one bit in color corresponds to a change in the base color of 1/256 of the possible range, or 0.4%, which prevents the human eye from noticing image distortion. There are modifications to the LSB that change the least significant 2, 3, or even 4 bits in the color byte. In this case, even in the worst case, the change in the base color is 16/256, or 6.25%, which is also quite imperceptible to the human eye. Modifications may be applied to make the message more difficult to identify, such as inserting into only one color byte.
The method has good capacity compared to other methods. For a 24-bit RGB model, each image pixel can contain 3 bits of a secret message (three bytes of color are changed, the byte for transparency is not changed). Thus, using the LSB method, approximately 2 megabytes of hidden data can be embedded in a 3048 by 2032 pixel digital image. Of course, this is true when it comes to formats that use lossless compression algorithms to store images, such as png and gif, and is not true for the jpg format. That is why the calculators above generate a stego image in png format.
The disadvantages of the method include its weak robustness - the method is very sensitive to distortions of the stego image.
Comments